Apache Kafka®️ 비용 절감 방법 및 최적의 비용 설계 안내 웨비나 | 자세히 알아보려면 지금 등록하세요
SIEM 설계자가 사이버 보안 솔루션을 보강하고 최적화할 수 있게 지원
오늘날 SIEM 아키텍트는 이질적인 레거시 사이버 보안 솔루션을 다양한 소스의 보안 데이터를 분석하고 이에 따라 조치를 취할 수 있는 통합 IT 플랫폼으로 전환해야 하는 과제를 안고 있습니다. Confluent의 사이버 보안 솔루션은 기존 SIEM 및 SOAR 솔루션을 보강하여 상황에 맞는 풍부한 데이터를 제공하고, 위협 탐지를 자동화 및 조율하며, 오탐을 줄이고, 조직이 실시간으로 위협 및 사이버 공격을 탐지, 분석 및 대응하는 방식을 혁신합니다.

"사이버 위협의 정교한 수준과 빈도가 지속적으로 증가함에 따라 기업은 효과적으로 감지 및 대응하고 환경을 보호하기 위해 신속하게 적응해야 합니다. Intel에서는 Splunk 및 Confluent 기반으로 확장 가능한 최신 CIP(Cyber Intelligence Platform)를 구현하여 이러한 요구 사항을 해결했습니다. 저희는 CIP가 미래에도 사이버 위협에 대한 최상의 방어를 제공할 것으로 믿고 있습니다."
Brent Conran, Intel 정보보호 최고책임자(CISO)
SIEM 플랫폼의 가치 극대화
SIEM의 기반이 되는 세 가지 요인은 규모, 속도, 비용입니다. 점점 다양해지고 빨라지고 방대해지는 보안 데이터로 인해 기존의 SIEM 기술은 더 이상 정보 보안(InfoSec) 팀 및 보안 운영 센터(SOC)의 현재 요구사항을 처리하기 어렵습니다. 오늘날 대부분의 조직은 SIEM 벤더로부터 보다 자유로워야 한다는 사실을 알고 있으며, 다양한 도구와 분석 목표를 활용할 수 있는 능력을 갖추고 있습니다.
최고의 실시간 스트리밍 데이터 인프라와 사이버보안 플랫폼을 결합하면 사일로를 제거하고 상황에 맞는 풍부한 데이터를 제공하여 상황을 보다 잘 인식할 수 있습니다. Confluent를 사용하면 세계 정상급의 데이터 수집 및 실시간 분석 역량을 확보하면서 비용과 규모를 최적화할 수 있습니다.
Confluent가 SIEM 최적화에 도움되는 방식
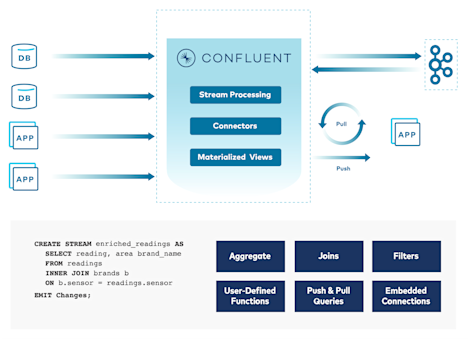
일괄 처리에서 스트림 규모의 실시간으로 전환
실시간 SIEM 파이프라인으로 차세대 사이버보안 데이터 인프라를 설계합니다.
- Splunk, Elasticsearch, SNMP, Syslog, AWS Cloudwatch를 비롯해 120개가 넘는 사전 구축된 커넥터를 활용하여 센서 데이터와 보안 이벤트를 수집, 집계, 저장할 수 있습니다.
- 매일 조 단위의 메시지와 페타바이트 수준의 데이터를 손쉽게 다루고 수 밀리초 내로 처리할 수 있습니다.
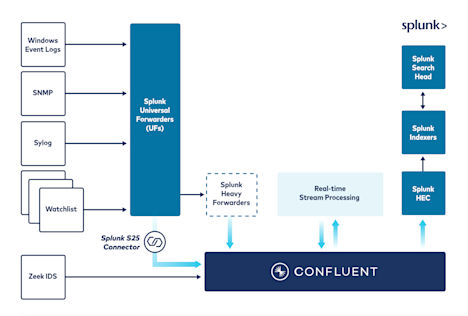
데이터 품질 향상과 위협 탐지 및 해결 시간 단축
데이터의 큐레이팅, 강화 및 정규화를 통해 에지 또는 수집 지점에서 위협 감지 및 데이터 엔지니어링을 수행하여 상황에 맞는 풍부한 통찰력을 얻을 수 있습니다.
- 정교한 스트림 처리 및 단일 메시지 변환(SMT)을 사용하여 보다 광범위한 위협 및 이상 항목 탐지를 지원합니다.
- 사고 감지 및 조사에 기여하지 않는 이벤트를 억제 및 마스킹하여 노이즈가 많은 데이터를 필터링합니다.
- 에지 및 수집 지점에서 처리를 진행하게 하여 지연을 줄이고 더 빠르게 통찰력을 얻을 수 있습니다.
- ML/AI 모델을 더 빠르게 훈련하고 프로덕션 단계로 더 빠르게 가져와서 보다 광범위한 실시간 위협 탐지를 지원합니다.
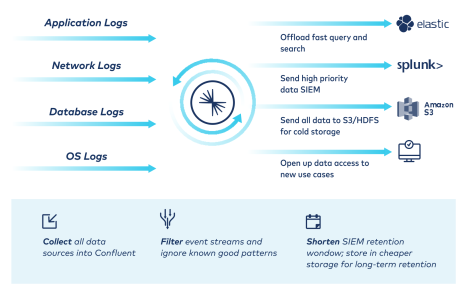
데이터 인덱싱, 분석 및 저장 비용 절감
비용, 유연성 및 가시성 간에 균형을 맞춰야 하는 데이터 저장 및 분석 비용의 증가가 미치는 영향을 완화합니다.
- 이용률, 볼륨 기반 가격 책정이 수반되는 수집 및 인덱스 볼륨과 전반적인 라이선싱 비용을 줄여줍니다.
- 독점 중개 전달자의 필요성을 줄여 Splunk S2S 커넥터를 통해 전반적인 운영 비용을 줄여줍니다.
- Amazon S3, Google Cloud Storage, Azure Blob storage, Snowflake 및 HBase와 같은 클라우드 스토리지 인프라에 대한 커넥터 및 계층형 스토리지를 통해 데이터를 비용 효율적인 목적지로 라우팅합니다.
- 네트워크 송신 및 수신 전에 필터링 및 집계를 진행하여 인프라 및 클라우드 비용을 줄여줍니다.
자유로운 선택 가능
전례 없는 유연성으로 소스 또는 목적지에 관계없이 다양한 데이터 옵션을 제공하여 종속성을 제거하고 최고의 기능을 활용할 수 있습니다.
- 소스와 목적지, 환경에 관계없이 데이터를 쉽게 통합하고 공유하여 데이터의 이식성을 확보합니다.
- 데이터 삭제 및 유실을 걱정할 필요 없이 원활하게 이전의 SIEM 도구에서 차세대 솔루션으로 마이그레이션할 수 있습니다.
- 최고의 도구를 활용하여 사이버보안을 강화하고 자유롭게 데이터에 액세스할 수 있습니다.
간소화된 아키텍처, 고급 기능
광범위한 연결성
광범위한 소스 및 싱크 사전 구축 커넥터를 활용하여 널리 사용되는 시스템 안팍으로 데이터를 쉽게 연결하고 이동할 수 있습니다.
고급 처리
Apache Flink와 단일 메시지 변환(SMT)을 통해 데이터를 지속적으로 처리하여 데이터를 인스트림으로 변환하고 강화합니다.
제한없이 보존
용량 제한없는 스토리지를 이용해 수개월 동안의 이벤트를 확인하는 분석 엔진에 필요한 장기간 데이터를 보존하고 저장합니다.
업계를 선도하는 보안
RBAC, 감사 로그, 비밀 보호를 통해 보안 침해 위험 및 다운타임을 최소화합니다.
유연한 아키텍처
지속적인 브리지를 구축하여 온프레미스, 클라우드 또는 에지를 비롯해 모든 곳에서 실시간 데이터 상호운용성을 확보합니다.
미래 대비형 디자인
지점 간 통합을 분리하여 새로운 소스 또는 대상을 통합할 수 있는 유연한 아키텍처를 설계합니��다.
Observability Solutions Built on Kafka

Datadog
Datadog은 Kafka를 기본 메시징 기술로 사용하여 매일 수조 개의 데이터 포인트에 걸쳐 데이터를 수집합니다. 자세히 알아보기

New Relic
New Relic은 Kafka를 사용하여 실시간 경보가 제공되는 실시간 모니터링 및 관찰 가능성 파이프라인을 쉽게 구축합니다.

SignalFX
SignalFX는 Kafka를 사용하여 초당 수십만 개의 메시지를 처리하는 최신 모니터링 및 분석을 실행합니다.자세히 알아보기

Honeycomb
Honeycomb은 Kafka를 활용하여 분산 시스템 간에 메시지를 안전하게 게시하고 수집함으로써 대량 이벤트 트래픽 유입을 처리합니다.

Salesforce
Salesforce는 안전한 다중 테넌트 시스템에서의 배송 및 주문 보증을 위해 Kakfa를 사용하여 엔터프라이즈 지원 이벤트 기반 계층을 구축했습니다.

Microsoft
Microsoft Azure는 데이터 수집 및 스트리밍에 Kafka를 사용하여 초당 최대 3천만 개의 이벤트를 처리하고 매일 수조 개의 이벤트를 처리합니다.
Additional Resources
Reference Architecture
Elastic and Confluent Technical Reference Architecture
Blog Post
Seamless SIEM: Osquery Event Log Aggregation
Intel Talk
Building a Modern, Scalable Cyber Intelligence Platform at Intel
Blog Post
How Confluent Can Help Optimize and Modernize Your SIEM for Better Cybersecurity
다른 Confluent 솔루션에 대해 알아보기
Confluent의 완전 관리형 이벤트 스트리밍 플랫폼이 어떻게 기업이 광범위한 사용 사례 전반에서 실시간으로 데이터 관리, 분석을 진행하고 통찰력을 얻는 방식에 혁신을 불러오고 있는지 알아보세요.